For some time now, attackers have been faking popular websites like YouTube to entice users into downloading and installing malicious software disguised as plugin updates or video codecs. I rcently found a page that is using the same technique to distribute a malicious executable through a fake UPS page.
The page is located at hxxp://www.retinamac.ru/UPS/. It has been up for at least three weeks and not yet blocked by Google Safe Browsing. At the top is a fake Firefox warning bar (the same type we analyzed earlier) for a missing plugin. It is interesting to note that the page shows the same fake bar to all browsers - it does not attempt to fake a specific implementation for say Internet Explorer or Chrome.
The page warns of a missing plugin. All links, buttons and images open a new popup to download JavaJREInstaller.exe. On 10/31, only 4 AV vendors were detecting the threat out of 43 vendors! Five days later, that count rose to 35 AV vendors. This illustrates how hard it is for AV to detect new threats.
A behavioral analysis of the executable shows that several executables are dropped into a temporary folders:
The page is located at hxxp://www.retinamac.ru/UPS/. It has been up for at least three weeks and not yet blocked by Google Safe Browsing. At the top is a fake Firefox warning bar (the same type we analyzed earlier) for a missing plugin. It is interesting to note that the page shows the same fake bar to all browsers - it does not attempt to fake a specific implementation for say Internet Explorer or Chrome.
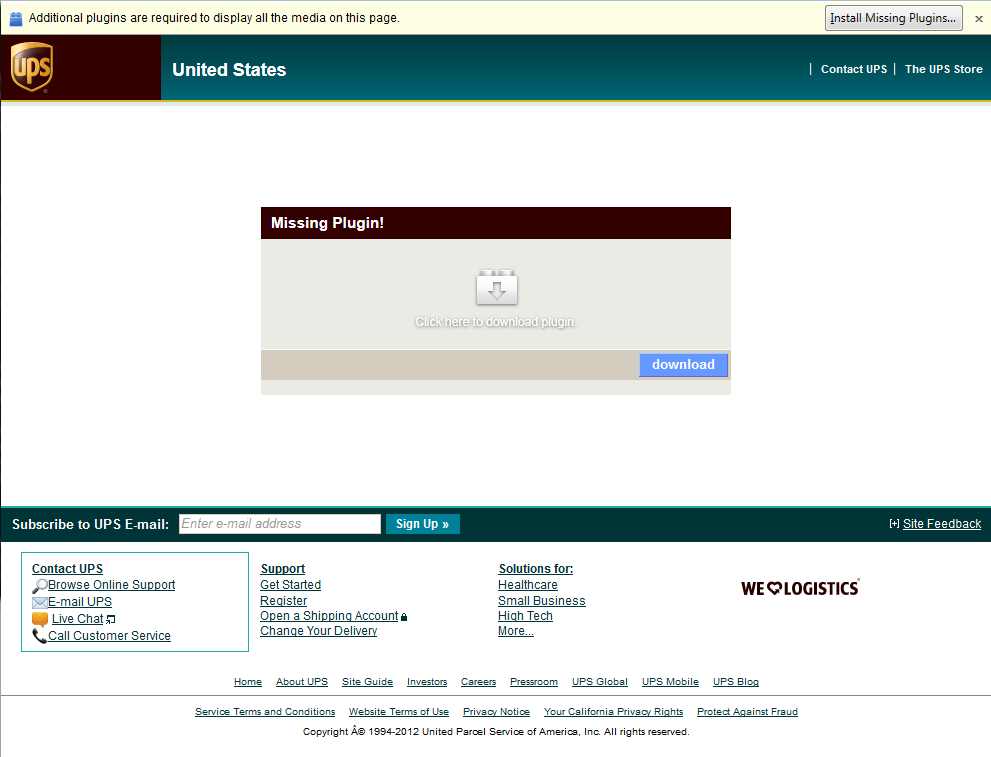 |
| Fake UPS website |
A behavioral analysis of the executable shows that several executables are dropped into a temporary folders:
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\00442734.exe
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\00445cfa.exe
- C:\DOCUME~1\ALLUSE~1\LOCALS~1\Temp\msuuioeyi.exe
- C:\Documents and Settings\All Users\Application Data\8CAFEE7F380FD13300008CAF61D8DA37\8CAFEE7F380FD13300008CAF61D8DA37.exe





