Recently we found several malicious executables with similar characteristics. These files were found on the following six domains:
- janashfordplumbing.com
- kalliskallis.com
- lowes-pianos-and-organs.com
- continental1.com
- foreigntire.com
- gjhimages.com
The URLs used, adhered to the following two formats:
- http://www.[domain].com/awstats6_data/[a-f0-9]{10}/?f=sm_main.mp3&k=[0-9]{15}
- http://www.[domain].com/images/[folder]/[folder]/[a-f0-9]{10}/?f=sm_main.mp3&k=[0-9]{15}
These six domains are otherwise legitimate sites that have been compromised and used to serve malicious content. While I didn't determine the vulnerability used to obtain control of these websites, all of them were misconfigured, allowing directory listings (viewing all files available in folders) and/or having AWSTATS publicly available.
The malicious files kept changing, with different signatures. Their behavior, however, was always the same and was identified as a botnet. When executed, the botnet hides itself in the Recycle bin and infects other running processes. It connects to over 50 IP addresses over UDP/16471 and TCP/16471. These IPs keep changing with each file and each execution.
The botnet always connects to xlotxdxtorwfmvuzfuvtspel.com through HTTP, but the domain answers with an empty response. You'll notice that the malware uses HTTP/1.0 with a Host header (not RFC compliant), often a good sign of malicious HTTP activity.
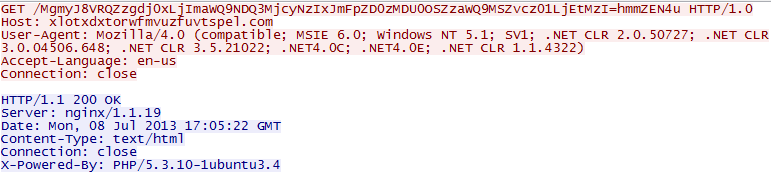 |
| HTTP request to C&C |
We found the malicious samples through Behavior Analysis, then used our log correlation to find the source of the malicious executables.





