 In the past few days I've had a number of people send me URLs that they received from friends on Facebook that seemed unusual and asked me what is this? In each of these cases, the answer was 'LikeJacking' - while this has been discussed in the security community for the last month or so (e.g., Sophos blog post), the general public seems fairly unaware of this technique. The term has been adopted enough, that there is a Wikipedia page for it, with a very straight-forward definition:
In the past few days I've had a number of people send me URLs that they received from friends on Facebook that seemed unusual and asked me what is this? In each of these cases, the answer was 'LikeJacking' - while this has been discussed in the security community for the last month or so (e.g., Sophos blog post), the general public seems fairly unaware of this technique. The term has been adopted enough, that there is a Wikipedia page for it, with a very straight-forward definition:
For those unfamiliar with Facebook's 'Like Button' - "The Like button enables users to make connections to your pages and share content back to their friends on Facebook with one click" additional details can be read here.
Many of the sites involved with LikeJacking are NSFW (contain nudity). However, below is a recent example of sites that I can safely take some screenshots of (sorry, no nudity on this blog):
Example: hxxp://tattooshaha.info/
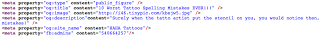
 Viewing the source of the site, we can see the META tags used for the information that will propagate to Facebook:
Viewing the source of the site, we can see the META tags used for the information that will propagate to Facebook:
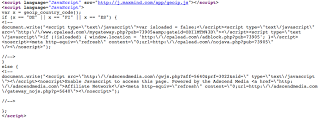
 And a transparent iframe to for the visitor to 'Like' the site:
And a transparent iframe to for the visitor to 'Like' the site:
 Why? Well the simple answer is to drive up the number of visitors to your site though Facebook 'Like' advertisement. For this particular example, clicking on the image directs users to hxxp://coolest-bathroom.info/tattoo/, and viewing the source of the page shows that JS source is loaded from cpalead.com:
Why? Well the simple answer is to drive up the number of visitors to your site though Facebook 'Like' advertisement. For this particular example, clicking on the image directs users to hxxp://coolest-bathroom.info/tattoo/, and viewing the source of the page shows that JS source is loaded from cpalead.com:
 The purpose of this campaign appeared to monetize click-throughs with cpalead.com:
The purpose of this campaign appeared to monetize click-throughs with cpalead.com:

I've seen this technique in play in a number of other LikeJacking campaigns, e.g.,
hxxp://www.101hottestwomen.com/
hxxp://102hottestwomen.com/
hxxp://103hottestwomen.com/video.html
hxxp://104hottestwomen.com/video.html
hxxp://105hottestwomen.com/video.html
hxxp://106hottestwomen.com/video.html
hxxp://107hottestwomen.com/video.html
hxxp://108hottestwomen.com/video.html
hxxp://109hottestwomen.com/video.html
hxxp://110hottestwomen.com/video.html
hxxp://111hottestwomen.com/video.html
The source of this one shows that if your visiting from Germany, Finland, or Spain IP you load from cpalead.com, otherwise you load from adscendmedia.com (CPA affiliate):
Blog Zscaler
Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Iscriviti'LikeJacking' - What Is It?
Grazie per aver letto
Questo post è stato utile?

Ricevi gli ultimi aggiornamenti dal blog di Zscaler nella tua casella di posta
Inviando il modulo, si accetta la nostra Informativa sulla privacy.




