We're seeing a massive campaign of malware distribution through Facebook look-a-like pages that started just before the new year.
These pages are using the free DNS and hosting provider .tk. This provider has been used for many spam and malware campaigns in the past. Here are some of the domains used:
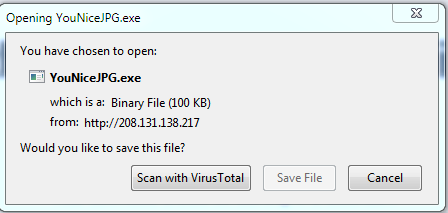
Only 1 AV vendor detects them as malicious at this time!
Looking at the source code, all the .tk domains load their content from another website through an IFRAME, with content from:
As usual, do not run files downloaded on random Internet pages.
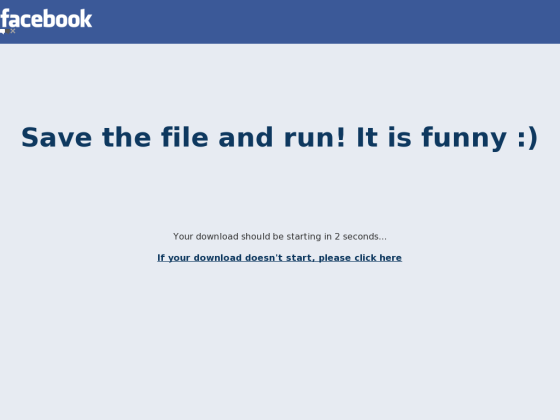 |
| Malicious page distributing malware |
- janejcfprofile.tk
- natalieclolyu.tk
- rosemaryrloveyouur.tk
- sabrinadjoyys.tk
- catherineufcitisfun.tk
- rosemaryiiqsuper.tk
- laurenaensweety.tk
- carlyqwowdv.tk
- YouWhoreGIF.exe
- YouNiceJPG.exe
- IamNiceBMP.exe
- IamNicePNG.exe
- YouFunnyJPEG.exe
- IamLolBMP.exe
- and may more
Only 1 AV vendor detects them as malicious at this time!
Looking at the source code, all the .tk domains load their content from another website through an IFRAME, with content from:
- liwwh.eqeki.com
- ngdy.hrdhm.org
- lsmxz.totyn.net
- cnpz.nukoq.com
- ...
- 208.131.138.217/132.html
- 208.131.138.217/208.html
As usual, do not run files downloaded on random Internet pages.