We’ve actually spotted in-the-wild exploitation of “Microsoft Internet Explorer ADODB.Stream Object File Installation Weakness” (Bugtraq ID 10514), a vulnerability first released in 2003. The exploit does get a little more modern as the code also targets vulnerability from 2009 (MS09-002). Here is a screenshot of the live infected page,
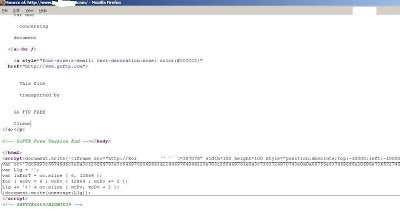
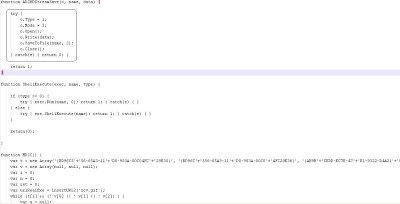

Virustotal results for the infected webpage show it being detected by 13 of 41 AV engines – not very impressive results for a seven year old vulnerability. It would appear that no matter how old vulnerabilities are, attackers will still try to leverage them as weapon. Hopefully most people have patched their systems at some point during the past seven years. Sadly, despite the age of the vulnerability, the use of JavaScript obfuscation has made this attack a challenge for AV vendors – a topic that we’ve discussed in the past.
Umesh





