
Centro risorse per le vulnerabilità di Log4j
Zscaler è qui per aiutarti a mitigare l'impatto di Log4Shell e prevenire altre vulnerabilità 0-day

Prendi parte a un webinar tenuto da esperti del settore e scopri come gestire l'impatto a lungo termine della vulnerabilità Log4j.
L'exploit Log4Shell permette agli aggressori di assumere il controllo dei dispositivi e scagliare una serie di attacchi contro dei bersagli vulnerabili.
Apache Log4j è una libreria open source per la gestione dei log utilizzata da milioni di applicazioni aziendali e servizi cloud. Ormai, gran parte delle organizzazioni ha aggiornato le proprie librerie Log4j per proteggere le applicazioni e le risorse più critiche, ma il suo uso diffuso può rendere difficile la ricerca completa all'interno di tutta l'azienda. Inoltre, gli aggressori più sofisticati potrebbero aver posizionato backdoor nei sistemi vulnerabili prima dell'applicazione delle patch, e questo consentirebbe loro di entrare e portare a termine attacchi in futuro.
Ecco perché c'è bisogno di una strategia di mitigazione a lungo termine per Log4Shell.
Ecco perché c'è bisogno di una strategia di mitigazione a lungo termine per Log4Shell.
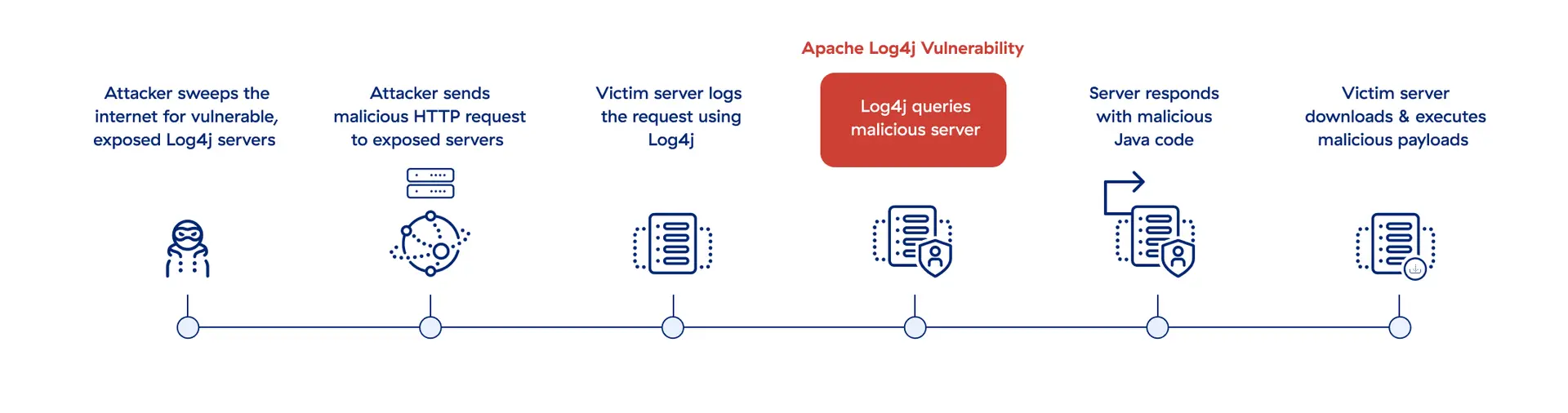
Blocca Log4j con lo zero trust
Prevenire gli exploit di Log4j con un'architettura zero trust
Un'architettura zero trust si basa su quattro principi fondamentali per nascondere le applicazioni vulnerabili, rilevare e bloccare le intrusioni e mitigare i danni degli attacchi eliminando il movimento laterale.
Eliminare la superficie di attacco esterna
Rendi invisibili app e server affinché sia impossibile comprometterli
Prevenire le compromissioni
Blocca le infezioni delle app web e gli exploit con l'ispezione TLS/SSL
Previene il movimento laterale
Limita la portata degli attacchi con lo ZTNA (Zero Trust Network Access) e la tecnologia di deception integrata
Previeni l'esfiltrazione dei dati
Blocca i tentativi di esfiltrazione dei dati utilizzando la DLP inline con l'ispezione TLS/SSL
Perché scegliere Zscaler?
Zscaler offre la massima tranquillità
Hai applicazioni e server Apache a cui non è possibile applicare patch? Collocandoli dietro Zero Trust Exchange™ di Zscaler, li nascondi agli occhi degli aggressori ed elimini le backdoor vulnerabili.
Scopri in che modo Zscaler Private Access™ elimina l'esposizione delle applicazioni vulnerabili.






