This is the eighth commentary in the series “Defining Zero Trust Security.”
Legacy network and security architectures served users suitably well in the pre-cloud and pre-mobile world. But no one lives in that world anymore (and hasn’t for decades). The old way had its day. So did the dinosaurs.
The new way of work demands a new architecture, one that both enables hybrid work and secures it. A Zero Trust Architecture (ZTA) is based on the fundamental principles of zero trust: Challenge everything, trust nothing.
Zero trust proposes a dynamic, ephemeral connection: Connectivity, whether user-to-application or application-to-application or workload-to-workload, is direct, and extant only for the (brief) duration of transit from point A to point B.
In a ZTA environment, Individual connections are isolated, ephemeral, and direct, supplanting the traditional notion of an “always-on, always-open” corporate network. Security is applied via proxy and tailored specifically to each instance of connectivity. The proxy—a cloud-based system, ideally replicated near each user location—inspects, assesses, and secures each arriving or departing packet of user data, effectively shielding an end user from attack and visibility to threat actors.
Zero trust – in modern practice – requires a distributed, cloud-edge-delivered service model. Contrast that with a legacy security model: Security appliance stacks require data traffic to be backhauled to a specific destination, where linear security processing bottlenecks that data traffic before it can (finally!) egress to the open internet. Zero trust brings security to the user, rather than the other way around.
In August 2020, after extended consultation with a consortium of cybersecurity industry experts, the US National Institute of Standards and Technology (NIST) issued its guidelines for a zero trust architecture (ZTA).[1] The NIST standard emphasizes two requirements for a modern ZTA: security is based on policy and security is delivered via proxy.
For example, a user logs on remotely and goes directly to a nearby cloud-based proxy that authenticates the user based on business policy as defined by enterprise management. From there, the user connects directly to authorized resources—and only authorized resources.
In the NIST-defined ZTA model, there is no trust associated with this because there is technically no network access granted—users connect only to specific, individual destination resources, such as a website or corporate application. Data coming in to the individual user is also challenged, with scalable security delivered at that proxy-based cloud service edge. Nothing bad gets in, and nothing bad goes out.
The Zscaler Zero Trust Exchange Platform: The NIST model in practice
Zero trust is a conceptual ideal. The Zscaler Zero Trust Exchange (ZTE) is its real-world manifestation. The Zscaler Zero Trust Exchange model serves as an unofficial reference architecture for the NIST ZTA standard.
The Zscaler ZTE architecture secures access to applications no matter where they live, no matter where the user may be, and regardless of device that user may choose. It’s often described as an “intelligent switchboard,” directing users to their desired (and authorized!) resource for the duration of their “call” (or, less analogously, connection). It requires that security be delivered close (read: at the cloud edge) to the entities being protected.
The Zero Trust Exchange runs across 150+ data centers worldwide, ensuring that the service is close to users, co-located with the cloud providers and applications they are accessing, such as Microsoft 365 and AWS. It guarantees the shortest path between users and their destinations, providing comprehensive security and optimized user experience.
ZTE in function
Importantly, and unlike legacy security models, the Zscaler ZTE architecture delivers its security processing (including internet access, advanced threat protection, data loss prevention, cloud app discovery, user activity visibility, zero trust network access (ZTNA), user behavior analytics, and comprehensive SSL inspection) in parallel. The ZTE employs Single-scan Multi-action (SSMA) technology to apply policy-based security services all at once. (Literally, all Zscaler security engines “fire” with each content scan.) In a legacy system, data traffic to and from the internet or datacenter must pass through multiple hardware stacks, enduring one security process after another before “approval” for ingress or egress. Those physical security stacks can contain more than a dozen individuals machines, each providing a disparate single function like firewall, URL-filtering, antivirus, data loss prevention (DLP), SSL inspection, sandboxing, global load-balancing, DDOS protection, VPN-concentration, and more.[2]
Back to the tollbooth analogy: Metaphorically speaking, traditional infrastructure is a ten-lane freeway that narrows to a single lane with a dozen tollbooths lined up in a row, with traffic throughput limited by the slowest data and the slowest machine…and it’s always rush hour. The cloud-served Zscaler ZTE is a ten-lane freeway that dynamically widens to as many lanes (100! 1000! 1,000,000!) and as many tollbooths as necessary to ensure optimized traffic throughput.
On the user device, the Zscaler Zero Trust Architecture connects via the Zscaler Client Connector (ZCC). The ZCC is a lightweight application that sits on the endpoint device and governs connection to the nearest cloud-edge based ZTE onramp.[3] ZTE then (immediately) applies corporate security policy to the direct connectivity request, subsequently routing traffic directly to the requested resource.
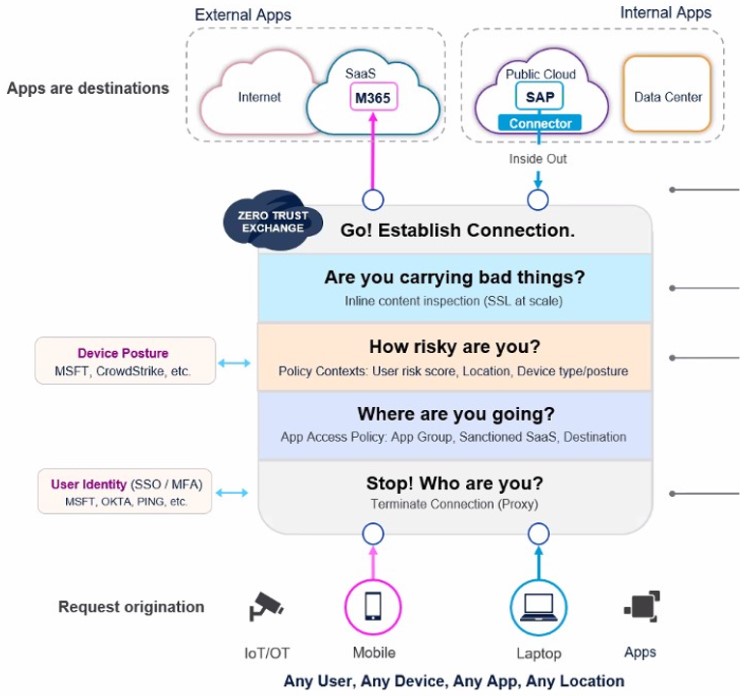
Figure 1. The Zscaler Zero Trust Exchange challenge stack
The “ZT” in ZTE
A ZTA like the Zscaler ZTE embodies seven key zero trust architectural principles that address major shortcomings of traditional legacy cybersecurity models:
- Zero Attack Surface
Hackers can’t attack what they can’t see. Unlike a legacy environment that requires users to connect to a central network, the ZTE has no inbound connections for threat actors to exploit. In a ZTE environment, nothing is visible to the outside world. - Zero Lateral Threat Movement
Traditional network architectures are only as secure as their weakest link: Once a hacker breaches a defense, that hacker has the run of the castle, and can move along the corporate network, infiltrating (and infecting) any and all systems attached to it. In a Zscaler ZTE environment, there is no network! Connectivity is ephemeral, disposable, and obscured: Shielded by the ZTE, a user connects directly to a resource, uses that resource, and disconnects from the resource. There is no permanence to the connection, which isn’t visible to the outside world. In this way, lateral threat risk is completely eliminated: Hackers can’t see a network (because there isn’t one), can’t see a (brief) connection, and -- in the rather preposterous event they compromise a system -- have no way to move to another system. - Cyber Threat and Data Protection
The cloud-based Zscaler ZTE is backed up by the industry’s most advanced threat protection technology and services. Data is constantly evaluated, and AI/ML provides additional layers of behavioral analysis. The Zscaler ZTE scales to accommodate traffic spikes, but also increases in complexity: It can analyze all TLS/SSL-encrypted data packets, finding proverbial needles in haystacks (even when those haystacks are hashed). That analytical detection capability works in both directions, preventing bad stuff from getting in, and preventing corporate data loss. - Risk-based Dynamic Policy
The cloud-based ZTE aligns security policy with business priorities: Administrators set controls by policy -- at a macro or micro level -- to reduce risk. Rule logic can be straightforward: Authorized users can connect only to the resources they are authorized to access. In this way, the ZTE blocks risky activity. - Zero Passthrough Connections
In a legacy network environment, users connect to the open internet by passing through a gateway. Similarly, incoming data reaches those users via a gateway, typically governed by a firewall. The more incoming traffic, the slower the performance, the greater the risk that something bad sneaks through. In the Zscaler ZTE, there is no pass-through connection, no impossible-to-secure firewall, no VPN: Every connection is direct, secure, and invisible to the outside world. - Multi-tenant service
The Zscaler ZTE architecture was “born in the cloud,” and designed from the ground up for multi-tenancy, with common security services distributed across Zscaler’s global cloud data centers. Such architecturally-optimized service delivery provides unprecedented reliability, availability, and scalability, while enabling cost savings, flexibility, and security to IT organizations. - SASE architecture with SSE-model security
The Zscaler ZTE architecture aligns with the Gartner-defined Secure Access Service Edge (SASE) architectural ideal and its Security Service Edge (SSE) security component model. Zscaler’s cloud architecture supports SSE’s key tenets: secure access to internet and web, secure access to SaaS and cloud, and secure remote access to private apps.[4]
[1] NIST defines a Zero Trust Architecture (ZTA) as “an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies.”
[2] Such slow gateways can drive users to “go rogue” and use direct-to-cloud connections for application access, bypassing corporate security entirely. The situation is exacerbated when those users are logging on via latency-adding VPNs.
[3] Born in the cloud, the ZTE has always been designed to optimize connectivity performance. With more than 150 datacenters spread around the globe, the Zscaler cloud edge is never far away from any users, regardless of geography.
[4] Gartner clarifies that “secure access to the internet” is delivered by Secure Web Gateway (SWG) functionality, that “secure access to SaaS and cloud” is the domain of a Cloud Access Service Broker (CASB) solution, and that “secure remote access to private apps” is part of a Zero Trust Network Access (ZTNA) service. In reality, those distinctions have become less important, since a cloud-edge delivered, SSE-compliant architecture delivers all in an integrated fashion. In fact, Gartner’s SSE definition subsumes SWG, CASB, and ZTNA classifications.
Related Content
The history, context, and co-opting of zero trust
So what exactly is it? The definition, context, and eventual practicality of zero trust
Zero trust’s impact: data-centric, scalable, practical, and secure
Risk, complexity, and no mistakes ever: the untenable absurdity of legacy security

