To learn more, visit our Zscaler Browser Isolation webpage.
If you’re ready to get a closer look, you can sign up for a 30-day trial.
A reverse proxy is a server, app, or cloud service that sits in front of one or more web servers to intercept and inspect incoming client requests before forwarding them to the web server and subsequently returning the server’s response to the client. This supports security, scalability, and performance for websites, cloud services, and content delivery networks (CDNs). A reverse proxy offered as a cloud service is one of the deployment modes of a cloud access security broker (CASB).
It’s easy to get these two types of proxy servers confused, so let’s break them down.
By sitting in front of a web server, a reverse proxy ensures no clients communicate directly with the server. A forward proxy (another CASB mode) sits in front of client endpoints to intercept incoming requests and ensure no servers communicate directly with a client. These different server types may sound functionally similar, but forward proxies usually depend on a software agent installed on endpoints to forward traffic, while reverse proxies do not.
“Reverse proxy server” is essentially a more formal term for a reverse proxy. (The same is true of “forward proxy server” for a forward proxy.) Today, we tend to drop “server” because it calls to mind hardware—like a physical box—whereas the technology often takes the form of an application or cloud service.
Sitting in the flow of traffic, a reverse proxy integrates with an organization’s authentication service (e.g., single sign-on). Once IT configures services and apps to transact with the reverse proxy, the proxy can operate inline without an agent. This offers a straightforward user experience, with incoming traffic to managed cloud apps and the like redirected to the reverse proxy automatically.
Let’s look at this process a bit more closely.
A reverse proxy can protect sensitive data (e.g., PCI data, PII) by acting as a middleman or stand-in for the server on which that data resides. Client requests are routed first to the reverse proxy, then through a specified port in any applicable firewall, and then to the content server—and finally, back again. The client and the server never communicate directly, but the client interprets responses as if they had. Here are the basic steps:
The reverse proxy can also scrub server responses for information that could allow a hacker to redirect to protected internal resources or take advantage of other vulnerabilities.
Reverse proxies are often built on open source software (OSS) due to the fact that it allows developers to access, modify, and distribute the source code. Many open source reverse proxies offer flexible and customizable features, allowing users to tailor the proxy according to their requirements.
For example, Nginx, Apache, and HAProxy are all reverse proxies that, through their OSS functionality, provide load balancing, caching, SSL offloading, and http request routing. OSS can also be ideal for security purposes, as it allows many eyes to review the code to identify vulnerabilities and propose fixes.
Reverse proxying, as a CASB deployment mode, is core to the security service edge (SSE) model alongside secure web gateway (SWG), zero trust network access (ZTNA), and other cloud-delivered security services.
.png)
Beyond SSE, common specific use cases for reverse proxies include:
Many of your employees may use multiple devices for work, including personal ones. Beyond that, plenty of suppliers, partners, and customers may need access to your internal applications on their own unmanaged devices, presenting a risk to your security.
You can install agents such as VPNs to manage devices your organization owns, but unmanaged endpoints are a different story. Third parties won’t let you install agents on their endpoints, and many employees don’t want agents on their personal devices, either. Instead, a reverse proxy offers agentless protection against data leakage and malware from any unmanaged device accessing your cloud applications and resources.
A reverse proxy can enforce data loss prevention policies to prevent accidental or intentional uploads or downloads of sensitive information to or from sanctioned cloud apps. Because it operates inline and inspects encrypted traffic (especially a cloud-based reverse proxy), it can ensure uploaded or downloaded data falls in line with your policies.
An infected file in a cloud service can spread to connected apps and devices—especially unmanaged devices. By agentlessly preventing uploads or downloads of infected files to or from cloud resources, a reverse proxy provides advanced threat protection against malware and ransomware.
By nature, reverse proxies also hide servers and their IP addresses from clients, which protects web resources from threats such as distributed denial of service (DDoS attacks).
Reverse proxies can be used to handle client requests that could otherwise overwhelm a single server with high demand, promoting high availability and better load times by taking pressure off the backend server. They mainly do this in two different ways:
With those use cases in mind, the advantages of using a reverse proxy fall into three main areas:
Reverse proxies offer notable security benefits when it comes to securing unmanaged devices and enterprise applications, but they bring notable shortcomings, too, such as:
Today, more organizations are turning to cloud-based browser isolation to avoid the limitations and breakage risks of reverse proxies while still enabling secure use of unmanaged devices without endpoint agents.
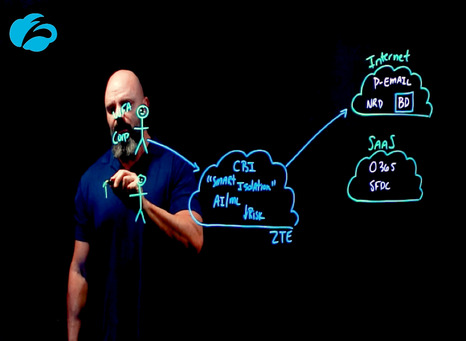
When a user accesses a managed cloud application, Zscaler Cloud Browser Isolation virtualizes the session and renders content in an isolated environment in the cloud, sending the session to the user as a stream of pixels. The user experience is identical to the native experience of that cloud app, except that CBI prevents unmanaged devices from downloading, copying, pasting, or printing the sensitive data found in the app.
This makes CBI the ideal way to support flexibility and productivity for your extended user base while preventing accidental leakage, malicious exfiltration, and malware proliferation via unmanaged devices.
Zscaler Browser Isolation™ provides unmatched defense against web-based data leakage and threats, powered by the industry's most advanced zero trust web isolation.
An Unmatched User Experience
Get lightning-speed connections to apps and websites with our unique pixel-streaming technology and direct-to-cloud proxy architecture. Users receive a high-performance stream of pixels in their browser, offering security without cutting into productivity.
Consistent Protection for Users Anywhere
Protect any user, on any device, in any location with a zero trust isolation policy that spans headquarters, mobile or remote sites, and highly targeted functions and departments.
Less Management Hassle
Deploy and manage in seconds, leveraging Zscaler Client Connector or an agentless option to route traffic through the Zscaler Zero Trust Exchange™ with its native Browser Isolation integration.
Universal Compatibility
Enjoy coverage for all major web browsers to suit user preferences. Cookie persistence for isolated sessions keeps users’ key settings, preferences, and sign-on information intact.
To learn more, visit our Zscaler Browser Isolation webpage.
If you’re ready to get a closer look, you can sign up for a 30-day trial.
What Is a Forward Proxy?
Learn moreWhat Is a Cloud Proxy?
Learn moreZscaler Browser Isolation
Visit our webpageWhat You Need to Know to Secure BYOD and Overcome Reverse Proxy Headaches
Read the blogWhat Is a Cloud Access Security Broker (CASB)?
Read the articleTop CASB Use Cases
Read the ebookA cloud proxy functions like a reverse proxy in many ways—client requests flow through the cloud proxy on the way to an internet address, and replies (e.g., permission to access a webpage) return through the proxy on their way to clients—but because the cloud proxy resides in the cloud, it isn’t confined to data center hardware like a conventional appliance-based proxy.
Plus, a cloud proxy gives you the benefits of universal application awareness, global scale, significant potential cost savings, great user experiences, and more.
To set up a reverse proxy, you must:
Proxy chaining involves forwarding traffic from one proxy server to another. This method leverages your existing proxy servers, with no additional changes to the network.