As in rugby, lateral speed has always been valued by attackers as a means to advance and dodge defense tactics and techniques. That's why hackers turn to exposed attack surfaces like VPNs to exploit flaws and vulnerabilities in order to move laterally until they reach high-value assets like credit card information for millions of customers. Motivated by espionage, state-backed hackers can also exploit zero-day vulnerabilities in VPN products as was recently described in CISA’s emergency directive, ED-24-01. If successful, a threat actor can move laterally, exfiltrate data, and establish persistent system access, potentially resulting in full compromise of target information systems.
ThreatLabz reconstruction of possible attack chain
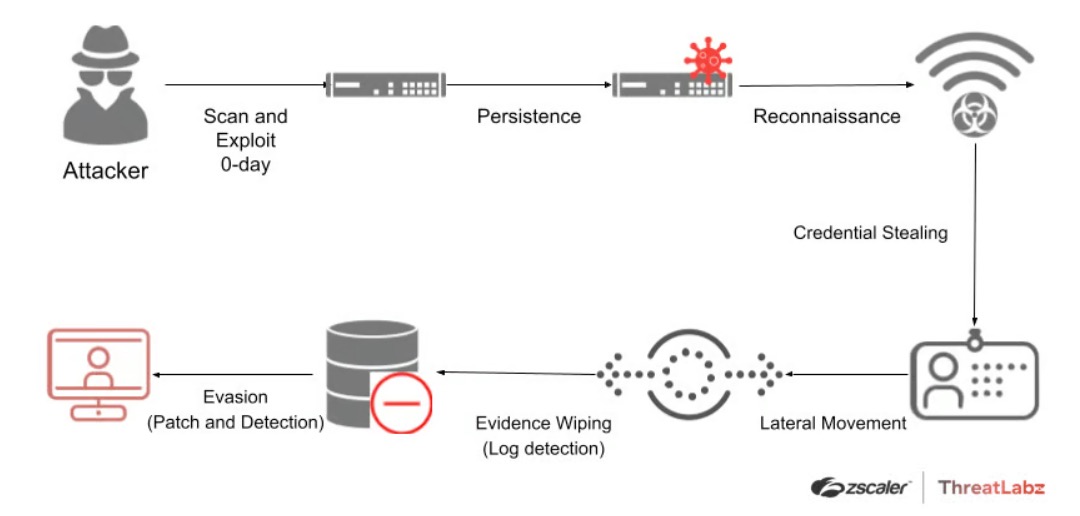
- Initial exploit: The attackers perform mass scanning for vulnerable devices and potential automated exploitation.
- Persistence: The attackers deploy different variations of web shells on the targeted devices after successful exploitation. After gaining an initial foothold, the attacker could steal configuration data, modify existing files, download remote files, and reverse tunnel from the devices. In addition, the attackers may backdoor configuration files and deploy additional tools.
- Reconnaissance: The attackers perform reconnaissance of the internal systems and applications through proxied connections.
- Credential stealing: The attackers inject custom JavaScript-based malware, called WARPWIRE, into a user login page to capture and exfiltrate plaintext credentials.
- Lateral movement: The attackers use the compromised credentials to move laterally and connect to internal systems via RDP, SMB, and SSH.
- Evidence wiping: The attackers are observed wiping logs and even restoring the system to a clean state after deploying their payloads.
- Evasion (patch and detection): In some instances, the attackers modify the integrity checker tool (ICT) to disable and prevent it from flagging any modifications or additions on the system to evade detection. By adding itself to the exclusion_list used by the ICT tool, the ZIPLINE tool used by the attackers is capable of bypassing ICT detection. As the attacks are discovered and publicized, they quickly adapt by modifying the tools to evade detection. As a result, new variants of the initial-attack are being observed in more recent attacks.
VPNs, whether hosted on-premises or delivered via virtual machines as a cloud access service, do not deliver a zero trust architecture. They extend networks for added functionality based on the principle of a shared network context. This configuration allows for easy access, as users and apps are both on the network. But easy access can be used to infect machines, since network-based controls have difficulty controlling lateral or “east-west” movement across the breached network. A single infected machine in a user’s home – or an infected workload in a public cloud – that shares the trusted network context can access all applications, giving it the potential to cripple a business.
A permanent solution to the growing list of VPN CVEs is a contemporary zero trust architecture to secure remote access to business applications. Zscaler Private Access (ZPA) is a cloud-native solution that replaces VPNs. It provides secure access with full deployment assistance in as little as 24 hours.
Learn more about how to get a free ZPA 60-day trial.

