These days, ransomware is not only on the minds of world leaders and company chiefs but also workers and their families as they discuss the latest high-profile attacks around dinner tables. The good news: we see more awareness and more action than ever before. The bad news: we’ve only seen the tip of the iceberg of the threat sophistication that the future has in store.
With this backdrop, the first global Zscaler Virtual CXO Summit titled, Resilience Against Ransomware: Zero Trust Best Practices for Threat Protection (view the on-demand recording) kicked off yesterday with CEO Jay Chaudhry setting the stage.
New threat vectors require a modern approach
After sharing mind-boggling stats–over $20B global estimated costs associated with ransomware recovery in 2021 and more than 4,000 ransomware attacks happen daily–Jay walked us through the failures of legacy network security architecture, noting how adversaries are using encrypted channels completely undetected across traditional network technology and unleashing attacks across common cloud-based apps. “Traditional firewalls were never designed to inspect SSL traffic so it is bypassed. It is like putting luggage on a plane without anybody inspecting it,” he said.
The best defense comes down to a modern architecture offering three simple, albeit profound components of zero trust: prevent compromise, prevent lateral movement, and prevent data loss. Zscaler’s cloud-native Zero Trust Exchange accomplishes all three, as depicted in the diagram below.
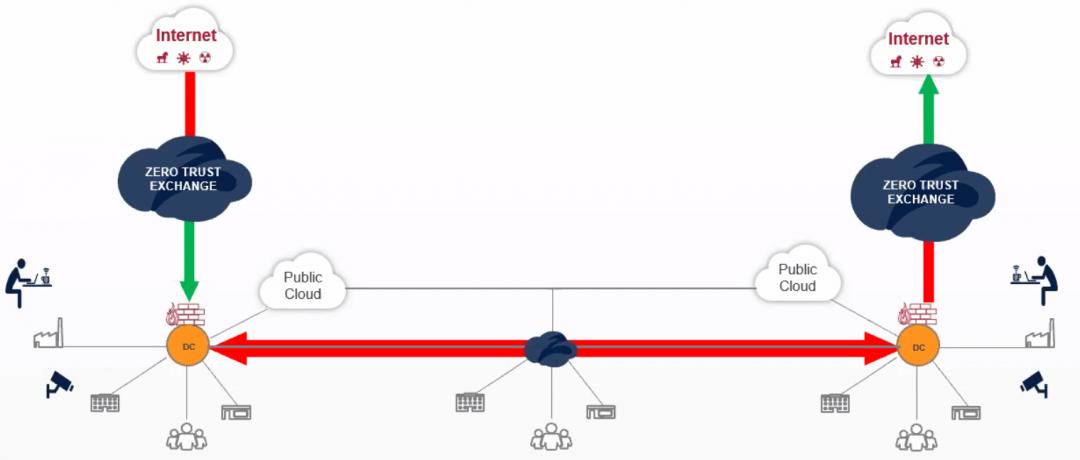
“It is wonderful to see the Biden administration focusing on zero trust as a core architecture. They emphasize the NIST definition because there are so many definitions of zero trust floating around...you either do network security or you do zero trust, you don’t really do both,” Jay said.
Design for the human
Next, guest Theresa Payton, one of the nation’s leading authorities on cybersecurity and the first female White House CIO, provided an eye-opening look at how ransomware syndicates are leveraging the very common and emerging technologies that are changing business and society like AI, cryptocurrency, IoT, and video conferencing to achieve their goals.
Payton cited a McKinsey study that found that in the last 19 months of the global pandemic, technology transformation roadmaps accelerated by seven years. And we went into the pandemic with technical debt. The combination of the two, she pointed out, is why it’s no surprise we’re all stretched thin and fatigued.
Payton shared an assortment of lessons and fascinating stories from her time at the White House. She claims we need a mind shift to fight cybercrime and not just throw money at the problem. Her key realization: Cybersecurity mostly ignores human nature, focusing on the systems and networks. End users are told to adapt. Cybercriminals, meanwhile, can “teach a masterclass in human behavior.”
She shared three core principles that will endure regardless of the technologies and innovations you have underway:
- Understand what drives human nature and your user stories encompassing executives, employees, and customers, and integrate that knowledge into your cybersecurity roadmap.
- Study your adversaries using decoys, honeypots, and dummy data. Then create user stories for them and profiles for both groups using behavioral-based analytics.
- Beat cybercriminals at their own game by creating “unexpected designs” (e.g, create a separate non-public domain name for fund transfers) and use AI and behavioral-based analytics to help create a force-field around your users.
Manipulation campaigns along with misinformation and disinformation (e.g, deep fakes, AI) are serious threats. Payton advises to be prudent and create a playbook that covers the worst things that can be said about your organization and executives and corresponding pre-debunking strategies that you can implement today.

Payton predicts that in 2022, we’ll see extended reality (XR) take off for global gatherings and it will unleash the internet of behavior that can be hacked. Yes, someone may one day crash your virtual reality one-on-one with your manager. Expect a “mini-black swan event” in the financial sector to set up a chain reaction that can potentially lead to a run on the banks. Lastly, driven by financial gain, cybercriminals will weaponize AI misinformation campaigns without human intervention.
In light of these advanced threats, Payton advises, “To be ready, know your user stories and focus on awareness and behavior. Model futuristic scenarios and practice playbooks.“
After Payton’s sobering depiction of what is to come, we pivoted to a pair of panels led by my transformation team experts, Brad Moldenhauer (CISO) and Lisa Lorenzin (CTO) who covered ransomware recovery and blocking attacks against proprietary systems, respectively.
Incident response is not only minimizing the impact on business but also on customers and society
Responding to and recovering from a ransomware incident instantly puts security teams in battle mode, requiring planning, coordination, and fast decisions. A detailed incident response plan impacts the overall costs and harms incurred and time to containment and helps reign in the chaos. Once the dust settles, you have to prioritize how you restart operations.
Michael Perrino, CXO REvolutionary, VP, CISO at CMA CGM, remarked, “Before you restart systems you have to make sure that everything is clean. Your Active Directory has to be clean as well as servers and workstations before you put them into production. Make sure you have EDR - endpoint detection and response - and MFA. And most importantly, as in our case, quickly give people access to core systems.”
Remarc Bognar, CXO REvolutionary, Head of Network Architecture, Norsk Hydro, recounted his experience: “It was obvious we were at war, and Scandinavians are an extremely democratic society so that means that decisions need consensus. In a crisis, this kind of model does not really work so we had a mind-switch and went into military action. We got our priorities from the business. But If AD is contaminated, you need to make your own priority on top of the high-level business priority.”
Bad guys are great at information sharing, while cyber shaming holds the good guys back
Lisa Lorenzin and her panelists kicked off the CXO Perspective panel examining a company’s crown jewels (a.k.a. data) and right-sizing the circles of trust you put around them. A printer has to trust a lot of different devices in order for people to use it efficiently, but a system that stores all of your critical data doesn't need to be accessible by everyone. Depending on who you ask, many different apps and data can be considered crown jewels. Regardless, when it comes to protecting it all against threats like ransomware, here’s what the experts said:
Steve Williams, CXO Revolutionary and Enterprise CISO, NTT Data: “I’ll quote the great 21st-century philosopher Mike Tyson, ‘Everyone has a plan until they get punched in the mouth,’ and I think cybersecurity is a combat sport, period. People have to move beyond the BCP/DR mindset of paper and tabletop exercises. Figure out what your landscape is, how you want to act, and don’t make it a consensus-based activity.”
Jeff Lund, CISO at Marsh and McLennan added: “My approach is to double down on information sharing within an organization and in between organizations. We want to be able to collaborate with IT partners, network teams, and desktop support teams and close the gap. If we can get past cyber shaming and do the basics well it would be a big win.”
Greg Simpson, CXO Revolutionary and former CTO at GE: “Figure out solutions for what your users really want. Often users ask for things they don’t really need because they are trying to accomplish a specific goal. If they just need access to a report on a daily basis, then you don’t have to give them access to the whole world - just get them the report. You want them to be able to do their jobs, and if you don’t help them, they will find a way to do it anyway. Build trust with your users.”
We have no choice but to deal with our vulnerabilities
Nicole Perlroth, New York Times cybersecurity reporter and author, delivered a spellbinding closing keynote.
“We are living in the Stuxnet era, where every nation-state, possibly with the exception of Antarctica, has been developing its own set of cyber capabilities, some for surveillance, some for sabotage, and an entire market has crept up to meet them. What we are seeing right now with Ransomware is in some ways inevitable, but also the culmination of what we’ve seen over the past decade,” according to Perlroth.
Perlroth covered a range of adversaries that we face, most notably China. More and more, Chinese APTs leverage zero-days, whereas in the past they relied on phishing. The country is telling their security talent they can no longer go to western security conferences. And if they find zero-days, they need to give the state the right of first refusal.
The scorecard for the US is mixed: “I believe the United States has the best offensive cyber capabilities in the world….but it has not been a sufficient deterrent, and we are one of the most targeted nations on earth.”
“In some ways, ransomware is a blessing in disguise because it is pentesting the United States right now and showing just how vulnerable we are and giving us very powerful visuals into that vulnerability,” she said.
In the following interview, Perlroth and I discussed how CXOs can effectively communicate the current threat landscape to boards, employees, and customers, and agreed that it comes down to soft skills. As executives in the cybersecurity field, we need to hire and promote people with technical skill sets who also have leadership, communication, and business skills. As Nicole said, “It’s no longer ok to elevate the best hacker in the room to leadership positions.”
Catch Perlroth’s complete talk and our Q&A session (as well as the other sessions) here, and check out her popular book, This Is How They Tell Me the World Ends: The Cyberweapons Arms Race, shortlisted for the Financial Times McKinsey Business Book of the Year Prize 2021.
Stay tuned for upcoming CXO Summits, and please join our Zscaler CXO Community on LinkedIn and share your reactions and ideas that may have been sparked by today’s dialogue. We’ve also picked up the conversation in the CXO REvolutionaries forum and welcome you to sign-up (membership limited to qualified CXOs) and participate.
What to read next
A CISO's perspective on ransomware payments

